SQL injection study notes
SQL injection learning notes
Injection from a macro perspective: 5 different types of injection
The classification of these five different types of injection is classified by different criteria for determining whether the injection is successful or not
- Boolean injection
- Union query: use union field
- Time Blind Note: Injection based on Time Lag
- Error injection
- Multi-statement query injection available
Examples illustrate
** Boolean injection **
The page only returns True and False two types of pages. Use different page returns to guess the data one by one.
http://test.com?id=1 and substring(version(), 1, 1) = 5
If the database version is 5.x, you can return to the page normally
** Joint query injection **
The criterion for judging whether the check-in is successful is whether other information is queried. This is the fastest way to get any data you want, but there is a prerequisite that the request can return the result of the sql query
http://test.com?id=1 UNION select 1,2,3,4 from INFORMATION_SCHEMA
** Time-based blind bets **
If a request does not return anything, or if the success result is the same, then we can not use Boolean or joint query to determine whether the injection here, so we need time blind injection
Select * from user where id = 1 and sleep(3)
If this statement is executed successfully, the query will be executed after 3 seconds. If we perceive a time delay at the front end, it means that the sql injection was successful
** Error type injection **
This type of injection is relatively rare, and the front end needs to be able to display some SQL error messages, which requires the back end to directly return the error results to the front end
Typically, the duplicate key of group by reports an error.
** Multi-statement query injection **
The most dangerous type of injection can execute multiple statements, which means we can also perform operations to update the database
http://test.com?id=1; update set name = ‘1’ where id = 1
The two most important steps of SQL injection
- Found points that can be injected. If an error is reported, if we enter 1, we can query normally, and if we enter 1 ', an error will be reported, indicating that there is a sql injection problem here
- Construct the original injection statement. Try to close the original statement and execute your own content by guessing the sql statement in the backend
Use time blind injection to bypass error-free (Boolean) echo-free (joint) scenarios
Definition: By injecting specific statements, through the physical feedback of the page to the request, to determine whether the injection is successful, such as injecting sleep statements to observe the loading time of the page to determine the injection point.
It is suitable for scenarios where the injection result cannot be obtained from the page, and even if the injection statement is successfully executed, it is not known

That is to say, we can splice the information we really want to judge before sleep. If Time Lag, it means that the previous judgment is correct. If there is no delay, it means that the judgment before sleep is a failure.
Common functions of time blind injection: substr, count, ascii, length, left, sleep
- General steps, first need to determine the existence of time blind injection here, so generally at the beginning is not and sleep (3), but or sleep (3), if you do feel a time delay, confirm that there is a time blind injection. (Or you are sure that the previous conditions must be true, you can also directly and sleep (3))
- If there is time for blind injection, add the conditions you want to judge before sleep, such as searching for a database called user
** Example: **
Get database length
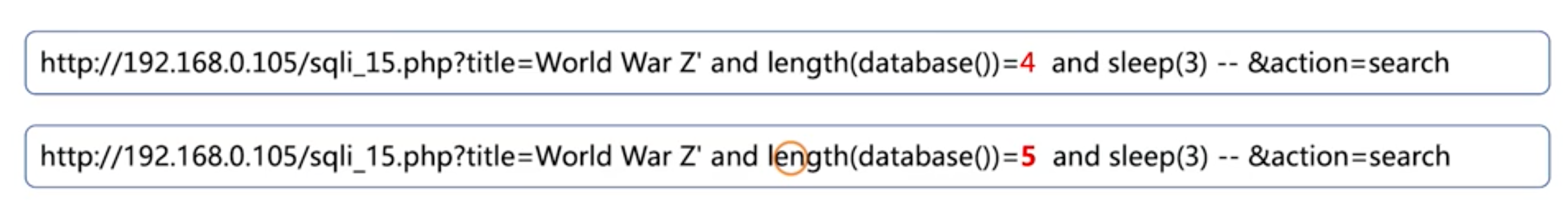
Get database name

HTTP header injection
If the header information of the HTTP request is not filtered or escaped, SQL injection is prone to occur during direct interaction with the database. Some webapps will obtain user access records, IP, hostname and other information from the header information
For example, the server will obtain user-agent information from the header and insert it into the database.
We guess that the injection statement in the backend is “insert into user values (” + use-agent + ") "
Then we can try to modify the user-agent header and replace x with 1); sleep (3) #
If there is a Time Lag, the injection is successful
If the statement is "insert
If the statement is "insert
Error injection
MySql error injection is mainly the use of MySql some Logical Vulnerability, such as BigInt large integer overflow.
MySql error injection can be divided into the following types:
- Data type overflow such as BigInt
- Xpath syntax error
- count () + rand () + group_by () causes duplicates
- Spatial data type function error
Prerequisite knowledge: preparatory function
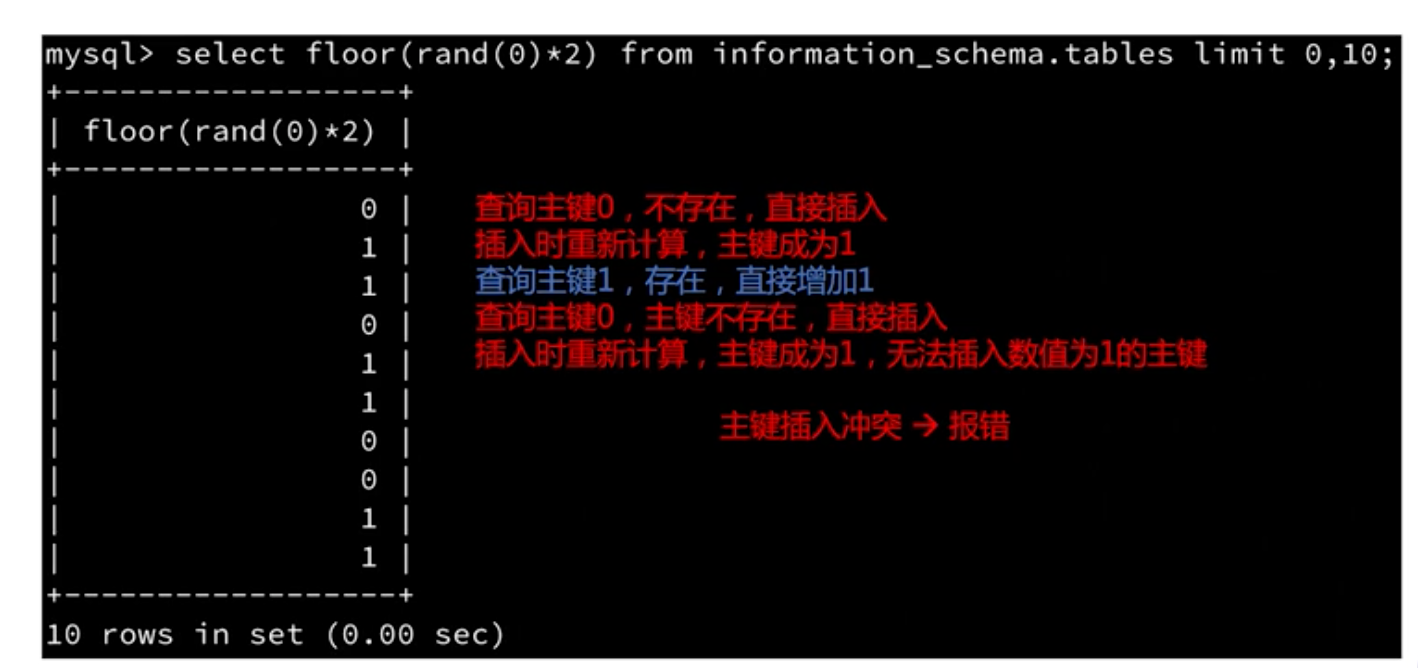
- rand (N): Returns a random number. If the parameters are passed, the generated random sequence will also be figured out when N is the same
- floor (x): return an integer not greater than x
- count: return the number of datasets