Introduction and Examples of VPN
Recently, I read an article about the principle of VPN and found that its connection establishment process is somewhat similar to HTTPS, and both of them encrypt data for communication.
Record the VPN connection establishment process here. If you want to compare the difference with HTTPS, you can see my other blog: https://sunra.top/posts/ ‘51308784’/.
What is VPN used for?
Some companies have multiple data centers and need to connect multiple data centers, or need to connect the work room and the data center. What should I do?
The first way is to go to the public network, but the public network is too insecure, and your privacy may be peeped on by others.
The second way is to rent a dedicated line to connect them, which is the practice of local tyrants and costs a lot of money.
The third way is to use a VPN to connect, which is a compromise, secure and inexpensive.
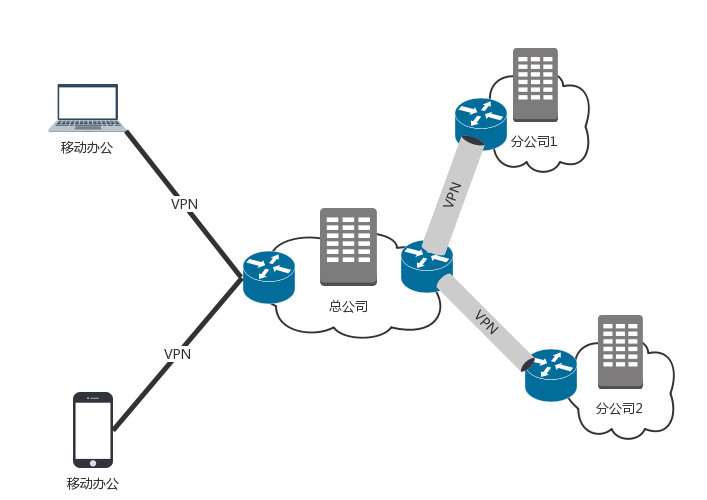
VPN, full name ** Virtual Private Network **, ** Virtual Private Network **, is to use an open public network to establish a dedicated data transmission channel to connect remote branches and mobile workers.
How VPN Works
VPN emulates a point-to-point dedicated line on the public network through tunneling technology. It is a technology that uses one protocol to transmit another protocol. There are three protocols involved: passenger protocol, tunnel protocol, and bearer protocol.
Let’s take the IPsec protocol as an example to illustrate.
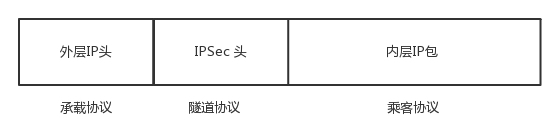
At the beginning, it was said that it is too insecure to use the public network directly, so let’s take a look at a very secure VPN, IPsec VPN. This is a secure tunnel protocol based on the IP protocol. In order to ensure the security of information on the public network, a certain mechanism has been adopted to ensure security.
Mechanism 1: ** Privacy **, to prevent information from being leaked to unauthorized individuals, and to ensure the privacy of data by encrypting the data from plaintext to unreadable ciphertext. When talking about HTTPS, it was said that encryption can be divided into symmetric encryption and asymmetric encryption. Symmetric encryption is faster. Once a VPN is established, a large amount of data needs to be transmitted, so we adopt symmetric encryption. But again, symmetric encryption still has the problem of how the encryption key is transmitted. Here, the Internet Key Exchange (IKE, Internet Key Exchange) protocol is required.
Mechanism 2: ** Integrity **, the data has not been illegally tampered with, by hashing the data, generating a data summary similar to a fingerprint to ensure the integrity of the data.
Mechanism 3: ** Authenticity **, the data is indeed sent by a specific peer, and the authenticity of the data can be guaranteed through identity authentication.
So how do you ensure that the other party is the real person?
The first method is to pre-share the key, which means that the two parties have discussed a secret code in advance, such as “The heavenly king covers the earth tiger, and the pagoda suppresses the river demon”.
Another way is to use a digital signature to verify. How to sign? Of course, I sign with a private key. Only I have the private key, so if the other party can use the public key in my digital certificate to unlock it, it means I am me.
Based on the above three characteristics, a protocol cluster of IPsec VPN is formed. This protocol cluster is relatively rich in content
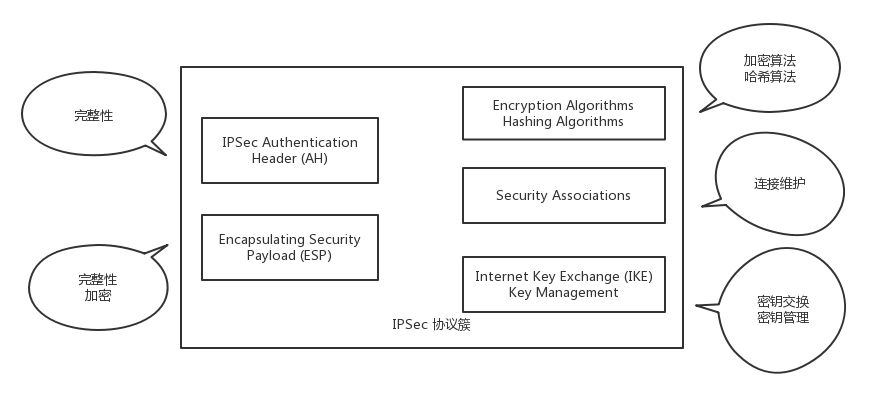
In this protocol cluster, there are two protocols, the difference between the two protocols is that the format of the encapsulated network packets is different.
A protocol called ** AH ** (Authentication Header) can only perform data summarization, not data encryption.
There is also an ESP (Encapsulating Security Payload) that enables data encryption and data summarization.
In this protocol cluster, there are two types of algorithms, namely encryption algorithm and digest algorithm.
This protocol cluster also contains two major components, one is the ** IKE component ** used by both parties of the VPN to exchange symmetric keys, and the other is the ** SA (Security Association) component ** used by both parties of the VPN to maintain the connection.
IPsec
Let’s take a look at the establishment process of IPsec VPN, which is divided into two stages.
** In the first stage, establish IKE’s own SA **. This SA is used to maintain an authentication and security protected channel to provide services for the second stage. At this stage, a symmetric key K is calculated through the DH (Diffie-Hellman) algorithm.
The DH algorithm is a more ingenious algorithm. Client and server level agree on two public prime numbers p and q, then Client randomly generates a number a as its own private key, server level randomly generates a b as its own private key, Client can calculate public key A according to p, q and a, server level calculates public key B according to p, q and b, and then the two parties exchange public keys A and B.
At this point, the client and server level can independently calculate the same result K based on the existing information, which is the symmetric key. However, in this process, the symmetric key has never been transmitted on the channel, only the material that generated the key is transmitted, and through these materials, the interceptor cannot calculate it.
With this symmetric key K, the next step is to establish an IPsec SA **. In this SA, both parties will generate a random symmetric key M, which will be encrypted by K and transmitted to the other party, and then use M for the data of the subsequent communication between the two parties. Symmetric key M has an expiration period and will be regenerated after a period of time to prevent it from being cracked.
IPsec SA contains the following content:
SPI (Security Parameter Index), used to identify different connections;
The encryption algorithm, hash algorithm and encapsulation mode discussed by both parties;
Life cycle, beyond this cycle, you need to regenerate an IPsec SA, regenerate the symmetric key.
Once IPsec is established, you can start packaging and encapsulating the transmission.
In the IP header, the protocol of the previous layer will be specified as TCP. ESP wants to encapsulate IP packets, so the protocol of the previous layer in the IP header is ESP. In the body of the ESP, the header of the ESP has the SPI negotiated by both parties, as well as the serial number of this transmission. Next is all the encrypted content. It can be decrypted with a symmetric key, and after decryption, at the end of the body, it indicates what the protocol inside is. If it is an IP, you need to parse the IP header first, and then parse the TCP header, which is the process of decapsulation after coming out of the tunnel. With IPsec VPN, the plaintext IP packets sent by the Client will be added with ESP headers and IP headers for transmission on the public network. Due to encryption, it can be guaranteed not to be stolen. After reaching the peer, remove the ESP header and decrypt it.
The similarities and differences with HTTPS
The similarities between the two are divided into two processes:
The public and private keys of HTTPS have been applied for in the CA in advance. The public key will be sent to the other party along with the certificate, and the private key will be kept here. Then the second stage uses the generated three random characters to generate symmetric CDKEY, and uses symmetric CDKEY. Encrypt HTTP information;
And IPSec VPN is the first stage to generate a temporary private key by itself, and then the two sides exchange the temporary public key and a random string generated by each, and calculate a symmetric CDKEY K by the DH algorithm, but the symmetric secret key K calculated by the two is the same. K is the same, the second stage uses K to generate another aged symmetric CDKEY M to encrypt information.