IP Address and Subnet Division, and the Difference from Intranet
IP Address
Two-level IP
The initial IP Address is composed of two parts, namely the network number and the host number. Different network numbers specify the network segment to which the IP belongs. It marks the network to which the host or router is connected. Each network number is unique in the entire Internet. The host number marks the host or router, and each host number is unique in the network number to which it belongs. So each IP is unique in the Internet.
This type of IP Address is called a two-level IP.
IP Address = {< network number >, < host number >}
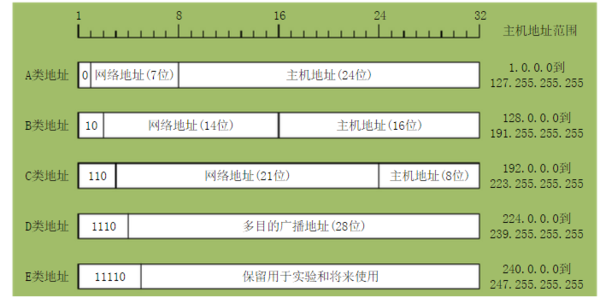
From the picture above we can see:
- A, B, C class address network number are 1, 2, 3 bytes long, and the network number field in front of each 1-3 bits of the category field, the values are 0, 10, 110.
- The host number fields of Class A, B, and C addresses are 3, 2, and 1 byte long, respectively.
- Class D addresses for multicast
- Class E address reserved.
- The addresses that can be assigned to classes A, B, and C are specified by the network number and the host number together, roughly (all 0 and all 1 addresses are reserved) twice as many as the latter (one bit difference), but a class A The number of addresses that can be assigned in an address is 256 times that of a class B address, because the number of bits in the host number looks up 8 bits.
When a unit applies for an IP Address, it actually applies for an address with the same network number, where each host number is assigned by the unit itself, as long as it is not repeated.
Some characteristics of two-level IP
- IP Address is a hierarchical address structure. ** There are two advantages to dividing it into two levels **. First, the IP Address management agency is only responsible for assigning network addresses when assigning IP Addresses, and the remaining host numbers are assigned by The unit that gets the network number assigns it itself. Second, ** routers only forward packets based on the network number connected to the destination host **, which will greatly reduce the size of the forwarding table that needs to be saved in the router and the time required to find routes.
- IP Address is actually a flag of a host or router interface (and usually we say that the port is different), when a host connected to two networks, he must have two IP Address, and because it is two networks, the two IP Address network number must be different, this host becomes the most home host.
- According to the Internet’s point of view, a network refers to a collection of hosts with the same network number. ** Several LANs connected by repeaters or bridges (working at the link layer) still belong to the same network **, because These LANs have the same network number, ** LANs with different network numbers must be connected by routers **.
All IP Addresses are equal. - The network number of the host or router inside the same ** LAN must be the same **.
** Routers always have two or more IP Addresses, and the network number of each address is different from each other **. - When two routers are directly connected, the interfaces at both ends of the connection can also not be assigned an IP Address, which is called an unnumbered network.
IP Address and MAC Address
MAC address is used by the link layer and the physical layer. It is an address based on physical reality. It is fixed and will never change when the device appears, while IP Address is a logical address. It is dynamically assigned when a device accesses a certain network. The IP Address of the same device is different in different networks.
IP Address is placed in the header of the IP datagram, including the source address and destination address. When handing over the IP data packet to the link layer, the network layer will use the ARP protocol to find the next hop route of the destination address. The MAC address, and then encapsulate it into the MAC frame and hand it over to the link layer. The link layer forwards the MAC frame according to the MAC address. During the entire routing and forwarding process, the IP Address is always unchanged, but the MAC address will continue to be replaced by the next hop MAC address of the destination IP in the current route.
Level 3 IP Address and Subnetting
I just said the second level IP Address, so why do you need the third level IP Address?
- ** IP Address space utilization is sometimes very low **, a class A address, the host number has 24 bits, the number of hosts can be allocated up to 10 million units, but in fact few units will be very good to use.
- ** Two-level IP Address is not flexible enough (note that it is not flexible enough, not insufficient, subnetting does not solve the problem of insufficient IP Address) **. Sometimes, an organization needs to open a new network in a new location, which is impossible before applying for a new network number.
In order to solve the above problem, in 1985, a subnet number field was added to the IP Address. This makes the second-level IP Address become the third-level IP Address.
The basic idea of dividing subnets is as follows:
- A unit with many physical networks can divide the physical network to which it belongs into multiple subnets. The network outside the unit cannot see that the entire network is composed of multiple subnets, because the external network number of this unit is still the same., is the same network.
- The way to divide the subnet is ** to borrow several bits from the host number as the subnet number **, and the host number also reduces the corresponding number of bits, so the second-level IP Address in the unit also changes from the second-level IP Address to the third-level IP Address.
- Datagrams from other networks still find the network where the unit is located through the network number. After entering the network of the unit, find the destination subnet according to the subnet number. Then the router of the destination subnet delivers the data packet to the destination host.
Subnet mask
From the header of the IP data packet is no way to see whether the source host or destination host subnetting, because the header of the IP data packet does not have any field indicating whether subnetting, so we must find another way, that is ** subnet mask **.
The advantage of using a subnet mask is obvious, that is, even a secondary IP address can use the subnet mask method to obtain the network number of the destination IP. ** Using a subnet mask, the method of obtaining a network number through a secondary or tertiary IP address is the same **, which is to “and” each bit of the subnet mask with the destination IP.
So how is the Subnet mask calculated? In fact, it is very simple, that is, the bit occupied by all network accounts (including network accounts and Subnet accounts) is 1, and the rest is 0.
After the addition of subnetting, you need to re-route forwarding table to maintain a multi-subnet mask, ** now there are three columns in the routing table, the destination network address, the subnet mask, the next hop address **, when a data packet over, row by row with the destination IP subnet mask, and the result if the same destination network address, the matching is successful, the next hop address of the column into the MAC frame encapsulation.
Packet forwarding when using subnets
- Extract the destination IP Address D from the header of the received datagram.
- First, determine whether it is direct delivery. Check each network directly connected to the router one by one: use the subnet mask and D of each network to perform a bit-by-bit “AND” to see if the result matches the corresponding network address. If it matches, the packet is delivered directly (first, use the matching route to convert D into a physical address, and then encapsulate it into a MAC frame) to complete the task, otherwise it is indirect delivery, execute 3.
- If there is a specific host route with destination address D in the routing table, deliver the datagram directly to the next hop route specified in the routing table, otherwise execute 4.
- For each row in the routing table (destination network address, subnet mask, next hop address), use the subnet mask in it to “AND” with D bit by bit, and the result is N. If N matches the destination network address, the data packet is passed to the next hop address specified in the row.
- If there is a default route in the routing table, send the datagram to the default route, otherwise execute 6.
- Report an error forwarding the packet.
Subnet and intranet
As mentioned just now, subnetting cannot solve the problem of insufficient IP Addresses, so what technology can alleviate the problem of insufficient IP Addresses? Here we will talk about ** NAT technology **.
NAT technology
NAT technology is simply the intranet IP (intranet IP Address is not applicable to the public IP, such as 192.168.0.1) address and public IP mapping, NAT is also divided into many kinds, such as static mapping, that is, one-to-one mapping, this way the number of internal private addresses on the number of external addresses, does not save IP resources, the second is dynamic NAT, the protocol maintains a pool of external IP, when the internal IP needs to send data When external, dynamically assign an external IP to him, somewhat similar to DHCP leased IP Address. The third is the most effective, also called PAT, which maps the IP + Port of the intranet to the IP + Port of the extranet.
Those who are interested can take a look.NAT与内网穿透。
CIDR construct supernetwork
The NAT mentioned above is to allow multiple hosts in the intranet to share a public network IP, which is somewhat similar to open source, while CIDR is more inclined to throttle. By breaking the classification of network addresses, network addresses are not limited to the ABC class. It is more flexible to assign network address numbers of different lengths to units with different needs to reduce unnecessary consumption of IP Addresses.
As early as RFC1009, it was pointed out that subnet masks of different lengths can be used in subnets, called Variable Length Subnet Mask (VLSM), and based on VLSM, a classification-free addressing method was developed. The official name is Classless Inter-Domian Routing CIDR (Classless Inter-Domian Routing).
The two main features of CIDR:
- ** CIDR eliminates the traditional Class A, Class B and Class C addresses and the concept of subnetting **, thus allocating IPv4 address space more efficiently, thus allocating IPv4 address space more efficiently, and in the new IPv6 Allow the scale of the Internet to continue to grow before use. CIDR divides the 32-bit IP Address into two parts before and after, the front is the ** network prefix **, which is used to designate the network, and the latter part is used to indicate the host, so ** CIDR makes the IP Address change from level 3 back to level 2 **.
- CIDR will ** network prefix ** are the same ** consecutive ** IP Address composed of ** CIDR address block **.
CIDR also uses address masks, which are used and generated in the same way as subnet masks.
It should be noted that the so-called CIDR does not use subnets, which means that CIDR does not specify several bits as subnet numbers in the address of 32. However, once a CIDR address block is assigned, it is still possible to subnet within the unit.
Since there are many addresses in a CIDR address block, the CIDR address block is used in the routing table to find the destination network. The aggregation of this address is called ** route aggregation **, and it can also be called ** to constitute a supernetwork **.
Assuming that an ISP has 206.0.64.0/18 have address blocks, which is equivalent to having 64 Class C networks, if we use CIDR, we can very flexibly assign address blocks of different sizes to units with different needs. At the same time, if CIDR is not used, each router that exchanges information with the ISP needs to save 64 routing information of the ISP, but with CIDR’s ** address aggregation **, each router only needs to save one 206.0.64.0/18.
When address aggregation occurs, then another problem is inevitable, that is, it is possible that the destination address of a request can find multiple matches in the routing table. At this time, we will use the longest prefix matching strategy., as the name suggests, is to choose the route with the longest prefix in the matching item.
Use binary search to find routes
After using CIDR, the lookup process of the routing table becomes more complicated due to the need to find the longest prefix match, so we need good data structures and advanced fast lookup methods.
One of the most commonly used is ** binary leads **. In this tree structure, the left-to-right bit values in the IP Address determine the path extending down from the root node layer by layer, and each path in the binary leads Represents each address stored in the routing table.
The construction process of the binary leads tree is also very simple. The input is all the IP Addresses in the current routing table. We find the ** unique prefix ** of each IP Address. The so-called unique prefix refers to all the IP Addresses in the table. Among them, the prefix is unique. As long as the unique prefix matches, only one route can be found.
By constructing a binary leads tree in this way, the maximum depth is 32 layers, which means that 32 bits must be used to find the only route in the routing table of this router.
Of course, it is not enough to get the prefix match through the binary leads tree. If we find the only record through the binary leads tree, we must also use the subnet mask and network prefix in the record to verify whether it is the network address of the destination address.