Secure Storage and Transmission of Tokens
What is Token?
What exactly is Token, I have not found a better definition, but looking back at its translation, I understand that the original name is the definition, Token is the token.
So what is a token?
Let’s first take a look at tokens in our real life.

Why is it a token? Because six doors can verify its authenticity, and at the same time six doors can obtain the identity of the person holding the token.
From here, we can give a general definition of Token:
Can be authenticated by a service.
The service can obtain user information from it.
That is to say, SessionID is a Token, and JWT is also a Token.
Token-based authentication process
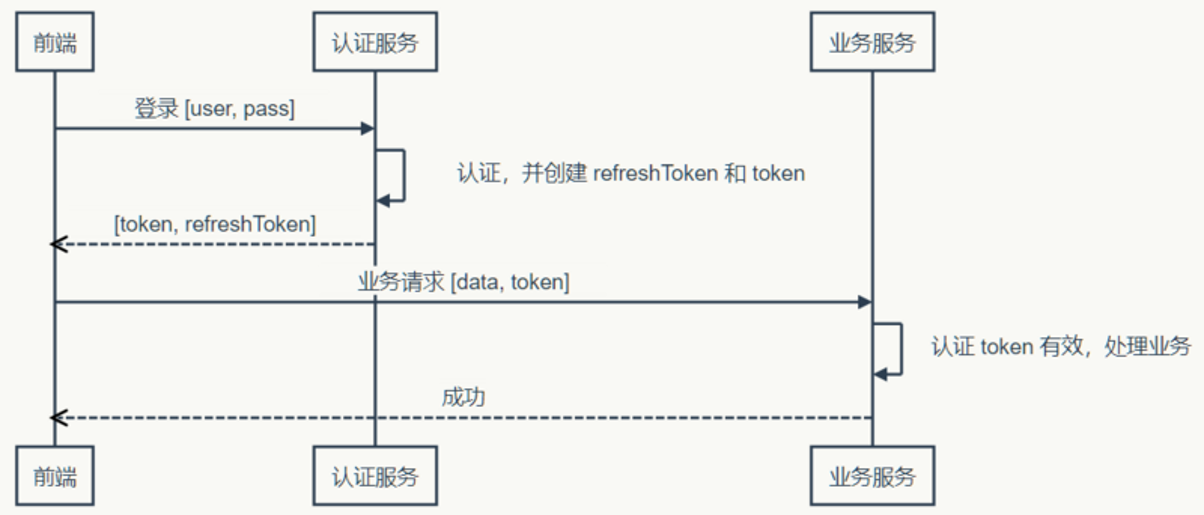
Roughly divided into several steps:
- The user sends a login request to the server, logging in with the username and password.
- The server verifies the correctness of the request after receiving it. If the authentication is successful, it returns a Token to the front end
- After receiving the Token, the front end stores it, and then each request brings the Token.
- The server takes out the Token from the request, verifies its validity and corresponding user information or permissions, etc. If it thinks it can initiate the request and then process it.
These steps seem simple, but there can be many upgrades, such as
The first step is to log in with the OAuth protocol, which is our common ** third-party login **. If you have doubts about OAuth, you can take a lookOAuth协议设计。
The second step If you choose to store the information in the server Session and return a SessionID, then the Token is the SessionID. If the server does not store any information, but chooses to encrypt and sign part of the user information back to the front end, you can use JWT.
There are many solutions for Token storage in the third step, such as Cookie, LocalStorage, SessionStorage, etc., and even USB Token. Consider the advantages and disadvantages of these solutions in terms of security, performance, cost, etc.
Also, although we can ensure that the ** of the Token cannot be tampered with ** through signature, how can we ensure that our Token is not eavesdropped during the whole process?
In addition, we can also consider why the second step sometimes returns two tokens. If you look at the OAuth protocol design mentioned above, you should have an answer to this question.
Comparison of several storage schemes for Token
Cookie
Cookie is the most familiar front-end storage solution. We are familiar with some of its features, such as same-origin restriction, automatic carry, etc. Then here are mainly several security aspects of its configuration:
- http-only: This parameter can only be automatically carried through the request to obtain cookies, there is no way to get through the script, so that you can effectively avoid the cookie being xss attack, and even if your page is accidentally injected into the script, you can not get your cookie.
- same-site: This attribute stipulates that cookies can only be obtained if the request is initiated from the same origin page. This is mainly used to defend against csrf, because if you can freely carry cookies as long as it is a request from the same origin, it is easy to suffer from csrf attacks. For example, if the attacker’s page is opened before the token expires, and the page automatically sends a request to the background, it will carry cookies.
- secure: This parameter allows cookies to be carried only by https requests. https should be one of the best ways to prevent man-in-the-middle attacks at present, which can effectively prevent your token from being eavesdropped.
Other front-end storage solutions
SessionStorage: The special point of sessionStorage is that even two pages under the same domain name, as long as they are not opened in the same browser window, their sessionStorage content cannot be shared;
LocalStorage: Share data between all tabs and windows of the same origin. The saved data exists for a long time. The next time you visit the website, the web page can directly read the previously saved data.
IndexDB: Similar to LocalStorage, but with a much larger capacity
Token protection at hardware level: USB
Tokens are stored on independent hardware, and important requests require users to fill in Tokens independently.
USB Key can also store digital certificates, the most common should be online banking U shield.
Comparison
SessionStorage has high security and can better defend against CSRF, but it is useless and limited to XSS.
LocalStorage and IndexDB are protected from the same origin, but once injected scripts are also dangerous.
USB Key security is high, belonging to the physical level of defense, but there is a certain cost.
Cookies are the most convenient, but they are the least secure by default. You need to enable http-only, same-site, secure, etc. to have higher security.
Secure Token Transfer with HTTPS
HTTPS is the protocol stack.
The top layer is HTTP, followed by SSL/TLS, and then TCP.
HTTP data packets encrypted by SSL/TLS before entering the TCP sending cache are called HTTPS.
Therefore, if you want to understand HTTPS, you must understand HTTP. The HTTP protocol itself is not complicated. Its complexity is reflected in various headers. These headers are designed for some applications, so this layer is called the application layer.
If you want to understand HTTP, it is best to understand TCP.
I have put together a few blog posts about TCP and HTTPS, which are the answers to some of my doubts about learning.
It might be better to take these questions with me when watching:
What is the HTTP protocol? The protocol used to obtain resources from the World Wide Web server, based on TCP, well known as port 80.
What is the TCP protocol? Transport layer reliable transmission protocol, caching the data continuously sent by the upper layer protocol and then packaging and sending it to the unreliable IP protocol, reliable transmission through a series of measures, Byte Flow Control and congestion control, and most importantly, connection-oriented characteristics, which are also important for encrypting data without confusion.
How does SSL/TLS encrypt data? Use symmetric CDKEY.
How to generate symmetric CDKEY? Why not use asymmetric? Symmetric CDKEY is generated with asymmetric CDKEY during each TCP handshake phase.
How to ensure the authenticity of the public key? certificate.
How to verify the validity of the certificate? Root certificate, certificate chain.
Here is the link address: